Cyber Security and Artifical Intelligence
Cybersecurity and Artificial Intelligence (AI) are intertwined nowadays. Cyber threats are becoming more and more sophisticated and AI technologies enable us to use powerful tech to boost security.
Service Description:
- AI-Powered Threat Detection: Minimise cyber risks by using big data analytics to recognize threats and provide real-time counteraction.
- Automated Incident Response: AI should be deployed in the automatic intervention and control of security threats and risks to the organization.
- Predictive Analytics: Since the use of historical data in developing the predictive analytic model can help pinpoint potential security threats, it can be confidently concluded that doing so will proactively help to enhance overall defense measures.
- Risk Assessment and Management: The current components of a successful risk management program include assessing, using AI tools, vulnerabilities and risks to prioritize security measures.
Data Protection and Encryption: Utilize contemporary AI approaches for the improvement of data safety and guarding of the critical data. - Security Awareness Training: Organizational AI readiness training programs that adopt AI influenced branching scenarios for mimicking the phish and increasing the recognition among employees.

✅ Threat Intelligence
✅ Vulnerability Management
✅ Machine Learning Solutions
✅ Fraud Detection and Prevention
Benefits
- Enhanced Threat Detection: The real-time speed and accuracy with which AI algorithms can process vast amounts of data makes it possible to spot potential security threats faster and more accurately than had been possible with traditional methods.
- Proactive Risk Management: Predictive analytics aid organizations to forecast and prevent risks from becoming dangerous security incidents before they get worse.
Automated Response: Cyber threats can be responded to automatically by AI driven systems, reducing damage and response time. - Improved Efficiency: Routine security tasks can be automated, pulling away the manpower from IT teams to focus on strategic or high risk security initiatives.
Data Protection: Data encryption and loss prevention strategies are strengthened by the help of AI in order to prevent sensitive information from being breached. - Adaptability: By learning from new threats, AI systems continue to learn and organizations can continue to adapt their cybersecurity measures to the ever changing risks.

Network & Cloud Security
At Walcha Networks we provide Network & Cloud Security Services to protect your business’ digital infrastructure. We provide solutions to keep your network and cloud environment secure; employing advanced security protocols, firewalls and intrusion detection systems. But we also maintain safe access controls and Real Time monitoring to find and remove any possible threats as they occur. We enable businesses to enter the digital realm confidently by utilizing industry best practices and cutting edge technologies to maintain compliance and mitigate the data breach and cyber attack risks.

Computer Vision & Smart Automation Solutions
At Last Gasp we are specialized in Computer Vision and Smart Automation Solutions that improve how businesses interact with their data and environments. Using computer vision technology, our machines are able to interpret and analyze visual information to perform applications including facial recognition, object detection and quality control in manufacturing. We couple smart automation with processes to automate repetitive tasks, accelerate operational efficiency and minimize human error. We integrate these cutting edge technologies to help organizations take new data insights and increase their productivity to innovate and grow further in such a highly competitive environment.

Vulnerability Management
The functionality of our Vulnerability Management service is to assess, and remediate security weaknesses in your organization’s systems and applications. To identify potential risks, we regularly conduct vulnerability assessments with state of the art scanning tools that help us identify before they can be exploited by cyber threats. We proactively considering prioritizing vulnerabilities on severity and potential impact of critical issues are addressed promptly. Through our continuing efforts of continuous monitoring, we enable the organizations to maintain a strong security posture, secure the sensitive data and meet required industry regulations.
Let us change the way you think about technology.
Our team of skilled developers is proficient in the latest technologies and frameworks to build responsive, scalable, and high-performance web applications.
Our latest projects
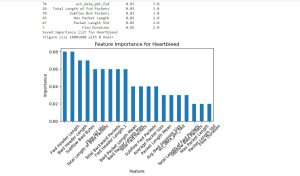
AI-Powered Cybersecurity Solution:
For our latest project we crafted an AI-Powered Cybersecurity Solution for use with a major financial institution. The provided system uses the power of machine learning algorithms to process enormous and current data in Real time to detect and take action to possible threats with highest speed and precision. Using advanced anomaly detection and advanced predictive analytics, the solution identifies vulnerabilities and mitigating risk ahead of exploitation. This has consequently raised the client's security posture significantly, reducing incident response times and mediating significant increase in overall protection against morphing cyber threats. This project highlights our commitment to infusing leading technology solutions into cybersecurity strategies so our clients can continue to perform effectively in a more digital world.
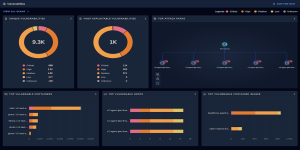
Vulnerability Management Program
In this there project, we aimed to implement a complete Vulnerability Management Program of a leading technology firm. We assessed their systems, applications, and network in depth to discover what it might be vulnerable to, and where. We identified which vulnerabilities we prioritized based on severity and potential impact and made that available to the organization so that they could address the critical issues quickly. We undertook ongoing monitoring and ongoing assessments that ensure that new vulnerabilities come in and are mitigated with speed. This has in turn greatly improved the client’s security posture and reduced potential cyber threats, as well as accrediting to industry standards. It is a project that shows we have completely turned to proactive security protection for our clients’ digital assets.

Project of AI
Our most recent project was to create an advanced Artificial Intelligence resolution for a retail customer which would help in increasing the customer experience and operational efficiency. Machine learning algorithms are applied to customer data and purchasing behaviors are predicted through real time personal product recommendations. We also integrated a natural language processing (NLP) chatbot to respond to frequently asked questions that can reducewait times and improve customer satisfaction. The use of AI technology has helped the client enormously with increasing sales conversion rates and also in improving the level of customer engagement, enabling fast business growth through AI. One outcome of this is our commitment to integrating cutting edge AI solutions which are realized results.

